

TROY Prismatix Forge™ UV Curable Flatbed Printers
Engineered with InkGenuity™ Premium UV Curable Inks to ensure optimal performance.


4001dw MICR Printer with WiFi printing.
Rated the #1 WiFi MICR printer for check printing with industry leading security.


Meet TellerCentral,
So much more than an ATM.
Expand your reach by enabling customers to print deposit slips, cashier’s checks, bank cards, and so much more.
Real world problems, solved.

MICR Check Printing
Create, print, and secure your checks with industry-leading OEM MICR technology, engineered by TROY and backed by HP.
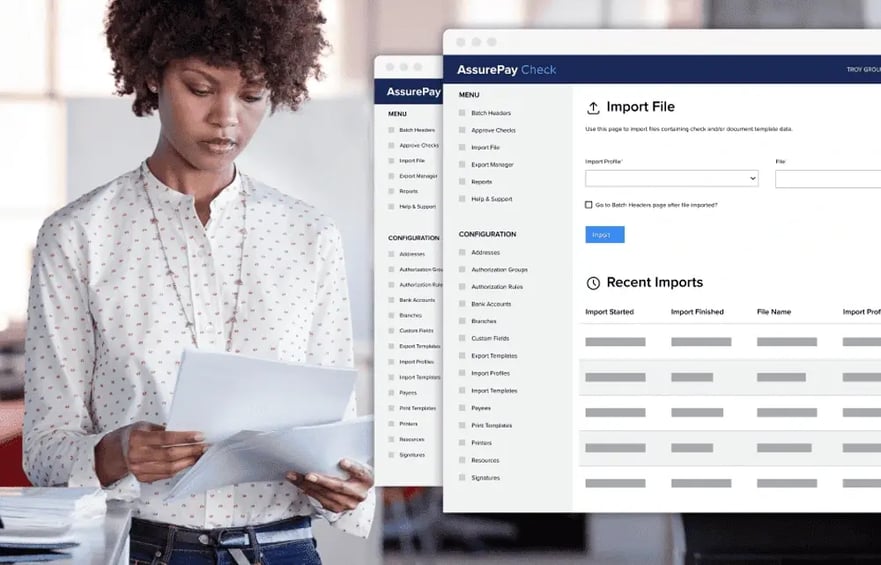
AssurePay Check Software
Create, print, and secure your checks with the industry leading, OEM MICR technology, engineered by TROY and backed by HP.
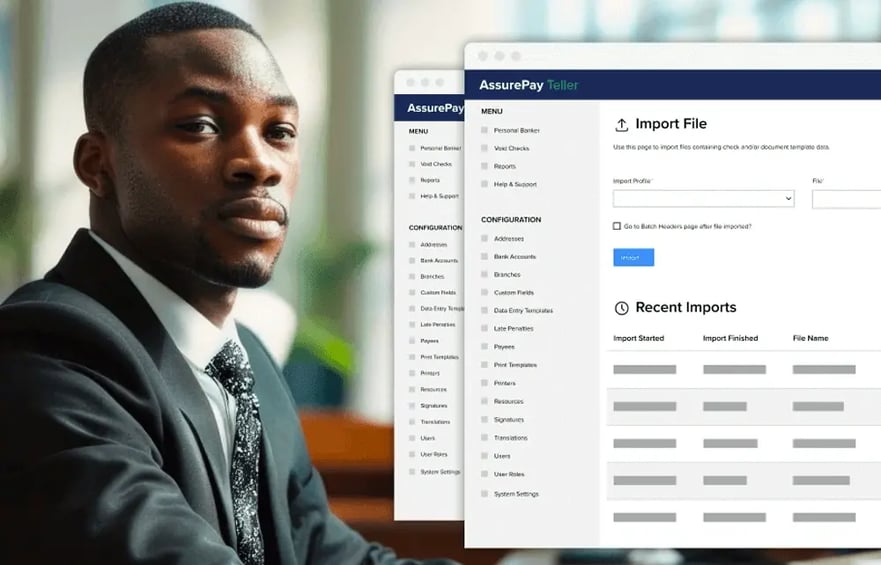
AssurePay Teller Software
Secure and efficient cloud-based software for bank tellers to streamline, manage, and print financial documents and checks.

Production Print
High volume printing meets 60 years of MICR innovation to offer the largest selection of production MICR printers in the world. Explore our diverse range of options and find your fit.

TellerCentral
Go beyond the ATM. Transform your branches from outdated to modern, self-service banking hubs that assist your customers with any transaction they need, wherever they are.

Pitney Bowes
TROY is proud to partner with Pitney Bowes, a trusted name in the mailing industry with a rich heritage spanning over 100 years.

SecureDocs Software
Prevent forgery, falsification, and alteration of your sensitive documents. Increase trust in your printed documents for vendors, customers, or enforcement officials.

SecureRx
Simplify paper scripts with the most trusted plain paper prescription printing software eliminating risk and lowering cost.

Industrial Inks
TROY Group offers a comprehensive range of inks tailored to various applications, including security, packaging, cardboard, and marking & coding.
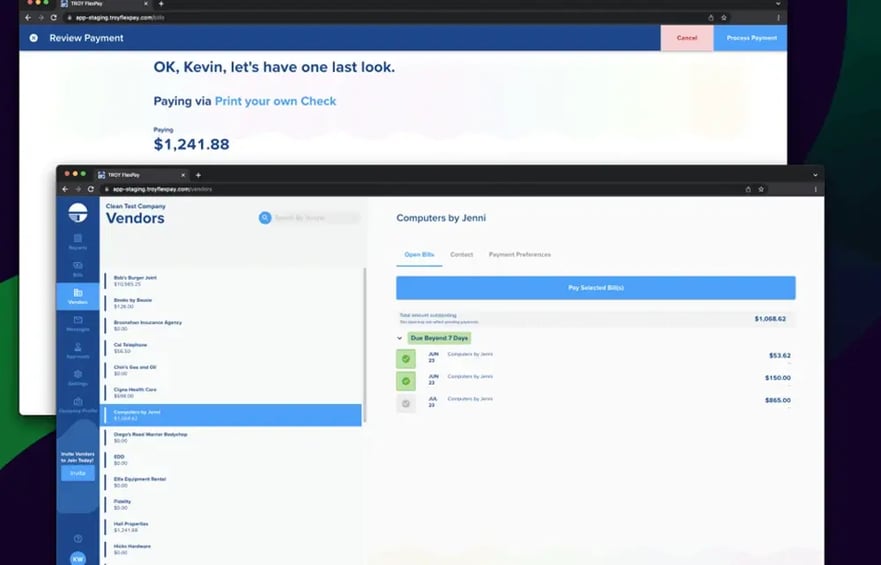
TROY FlexPay
Finally, a payments solution for QuickBooks that lets you pay invoices the way you prefer.
Trusted by thousands of brands.

Demand TROY solutions throughout your entire organization.

How can we help? Our experts work with you to create a tailored solution that solves your business needs.
Let's talk securityFully integrated products.
Run your business efficiently with hardware, firmware, and software that works together to handle your data security needs.

Your data, always secured.
Your data needs protected whether it’s on your network, sent digitally, or on a printed document.
Made and supported in the USA
USA made products, with USA based support and customer service dedicated to helping you.

Powerful OEM partnerships.
Unmatched quality, security, and reliability, all backed by the world's largest OEM manufacturers.

A global security company.
Customers in over 100 countries demand TROY as their go to partner for security solutions.
COMPLIANCE & SECURITY
Never fall below established standards.
-

ABA/ANSI
Exceed check printing standards for US financial institutions.
-
.png?width=80&height=68&name=_%C3%AB%C3%8E%C3%93%C3%88_1%20(1).png)
CPA
Exceed cheque printing standards for Canadian financial institutions.
-
%20(1)%20(1).png?quality=low&width=80&height=79&name=Layer_1%20(1)%20(1)%20(1).png)
HIPAA COMPLIANT
Our prescription solutions follow HIPAA compliant standards to protect health records.